[ad_1]
While getting ready the Online Routing Security webinar, I stumbled upon RFC 7908, that contains an outstanding taxonomy of BGP route leaks. I by no means checked whether or not it covers just about every attainable circumstance, but I found it a useful resource when arranging my ideas.
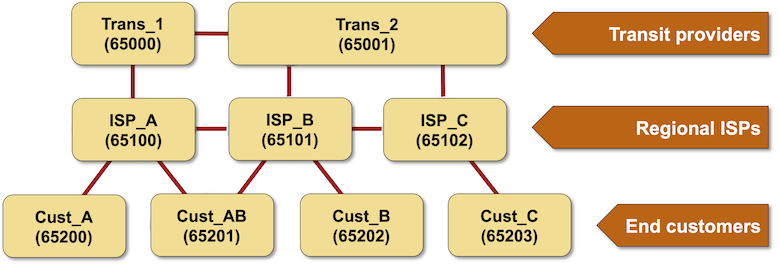
Let’s stroll by way of the many leak types the authors determined making use of the adhering to sample topology:
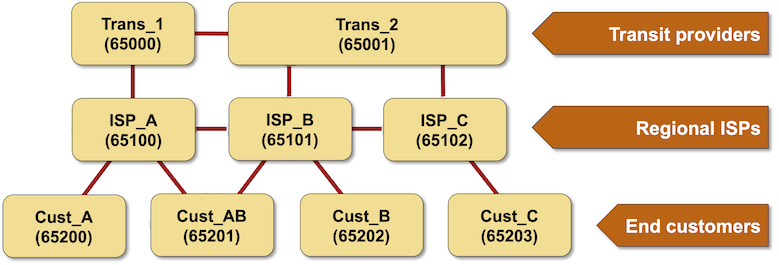
Hairpin convert: a buyer lacks output filters and propagates routes in between two service vendors (example: Cust-AB propagates ISP-A routes to ISP-B). Relying on the upstream connectivity of the ISPs, the route by way of the purchaser AS may outcome in the shortest AS route. Even even worse, quite a few provider suppliers prefer client routes around peer routes irrespective of AS path size
Lateral leak: a services company is leaking peer routes (illustration: ISP-B forwards ISP-A prefixes to ISP-C), and its peers commonly take them as best routes:
- AS route on a lateral leak is shorter than the paths likely by the transit providers
- No person in their ideal head would favor transit routes (where they are having to pay for targeted traffic or bandwidth) over settlement-cost-free peer routes.
Everybody concerned in a lateral leak should really be grateful that a sort soul supplies no cost transit connectivity. Regretably, that kind soul generally forgets to provision its peer one-way links accordingly, ensuing in congestion and client complaints.
Peer-transit leaks: a company service provider is leaking peer routes to its upstream transit provider (or vice versa). In our topology, ISP-B would leak routes in between ISP-A and Trans-2. The transit service provider would usually desire leaked routes (coming from its shopper), and the peer ISP would most likely decide on them because of to the shorter AS path length.
As just before, karma punishes the form soul giving cost-free transit with further website traffic expenses, and everybody gets yelled at thanks to inescapable link congestion. Not specifically a entertaining working day in the business.
Deficiency of routing policies (= filters) on EBGP sessions typically cause the abovementioned leaks. Now for some significant hitters:
Prefix re-origination: an autonomous process advertises 3rd-get together prefixes as belonging to by itself:
Last but not least, there is the accidental leak of interior- or additional-unique prefixes, normally resulting from a missing route map in an IGP-to-BGP redistribution point. We’re almost certainly working with this type of leak when anyone announces an further 20.000 routes and revokes them a number of minutes afterwards. Bonus points for model if individuals routes deliver the dimensions of the world BGP table above a components limit of core Online routers.
In the following website posts in this collection we’ll discuss individual leak types and tools you can use to keep away from them. In the meantime, read RFC 7908 and look at the World wide web Routing Security webinar.
[ad_2]
Source backlink